Cybersecurity Part 4: Surviving Ransomware

By Tony DePrato | Follow Me on LinkedIn
The scope of all the following arguments is for equipment owned by the school, or equipment approved to use at school. This post is not promoting policies for personal devices used solely at home, nor is this post addressing devices that may be used for entertainment or non-academic purposes.
Ransomware, in its most basic form, is self-explanatory. Data is captured, encrypted, and held for ransom until a fee is paid. The two most common forms of ransomware delivery are through email and websites.~ https://insights.sei.cmu.edu/sei_blog/2017/05/ransomware-best-practices-for-prevention-and-response.html
Ransomware is scary. Ransomware, once it begins to propagate, becomes more about survival and mitigation and less about prevention.
I have thought about how to advise K12 schools around the world how to prepare for ransomware. I have concluded that there are only two approaches everyone can follow: Reduce or Completely Remove Windows and Create Very Inconvenient Backups of Data.
Reduce or Completely Remove Windows
I decided to compile known types of ransomware. I stopped at 106 identified types. Here is a graph, and link to the sources, that demonstrate what operating systems are vulnerable:
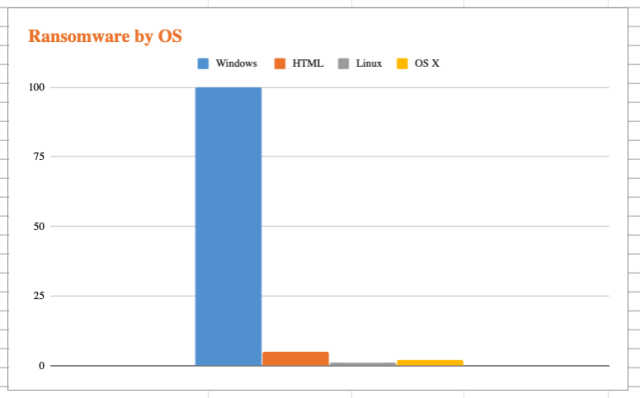
If you want to do the math:
- 106 Ransomware programs
- 100 Target Windows Operating Systems
- 93%-94% of Targets are Windows Operating Systems
- Using Windows is Riskier than Using other Systems
“Riskier” is a little weak in this case. It is very likely that Windows users will be a target, it is very unlikely that Apple and Chromebook users will be a target.
If the goal is to live in a relatively peaceful ransomware free environment, then the majority of end-users need to be using Apple or Chrome-based devices (Linux varieties are also an option for a subset of users).
There are tools for Windows that help defend and protect against ransomware. However, nothing is better than not being attacked at all.
Create Very Inconvenient Backups of Data
Every time I ask an IT director or IT manager about backups, they claim they are 100% compliant and 100% able to deal with any problems. I have never believed my planning was close to 100%, nor have I ever believed I could restore 100% of all data. I would say, at my best, I am 60%-70% certain that I can restore 80%-90% of data.
Data. Not operating systems and settings. Data. Not the software that was installed. Just all the data consisting of but not limited to documents, databases, movies, music, pictures, special configuration files, scripts and code, and the inclusive content of all websites.
There is only one question a person needs to ask to confirm if backups are safe from ransomware: “Can the backup be accessed right now if we need it?”.
If the answer is ‘Yes’, then backups are going to be vulnerable.
There should be at least two layers of backups. Layer one can be data that is backed-up and accessible on the network, in the cloud, and/or from normal workstations. Meaning, someone can sit down and create or restore a laptop, database, etc by following a workflow at their desk.
Layer two backups are inconvenient. These backups are stored outside of the normal network. These backups are scheduled and not even accessible by network administrators without taking extra steps. These backups require some level of multifactor authentication or even a physical lock and key.
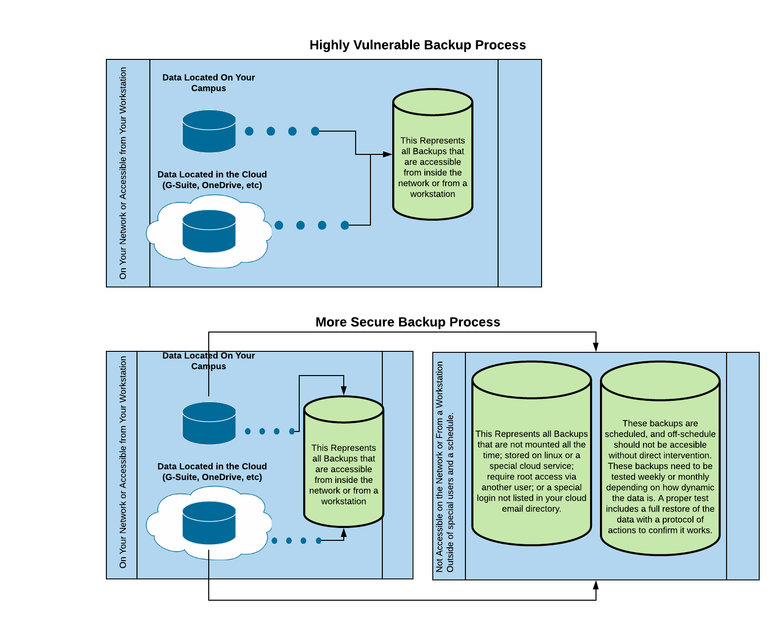
Layer two backups also need to be tested at least monthly (this is only recommended for K12 schools most businesses need to test more frequently; school districts would need to test very often and on a predetermined schedule).
Tests need to include:
- Data restoration
- Data access and use
- A scan for malware, ransomware, etc
- An iterative process to consistently reduce the size of backups
- An archival process to store data that will most likely never be needed, but is legally required to store
- Imagination. Because you never know where you will be and what the situation will be when you need to access these backups
A very low tech approach to a layer two back-up could include someone taking an external drive to the data source, moving the data manually, and then locking the drive in a safe. Do not overthink this, just start doing it and keep improving the process. If you can access these backups from your workstation, then those backups are vulnerable by definition.
If ransomware happens, and the data cannot be decrypted, this layer two data would be safe as it would be offline. Layer one backups may stay secure, but layer two backups will be secure unless you are victim of very bad timing.
The cybersecurity industry is rapidly developing better protocols for handling ransomware. Staying educated and studying cases is not only essential, but it should also be scheduled into the cycle of work at least once every 6-8 weeks.
The data above could change. An uptick in ransomware for Chrome or Apple of even 1% is enough to review internal processes and procedures. Until then though, get the number of Windows OS users down and make better backups.
Start Your Research Here
Ransomware: Best Practices for Prevention and Response
Source: IT Babble Blog and Podcast
You must be logged in to post a comment.